A Simple Guide to Authentication and Authorization Protocols.
Protecting Business Assets and User Data Through Robust Authentication and Authorization Strategies.
Secure business applications are critical to the success of any modern enterprise. With more and more businesses moving their operations online, securing business applications has become increasingly important to protect sensitive data and prevent unauthorized access.
When I started learning about this topic, I was immediately confronted with a wealth of information, including terms such as authentication, authorization, OAuth2, OpenID Connect, JWT, access token, ID token, refresh token, identity providers, and many more. As a consequence, I was unsure where to start.
Therefore, we will begin by examining each term individually and categorizing them to better understand the subject matter.
Authentication and Authorization
Authentication and authorization are key concepts in securing business applications. Authentication refers to the process of verifying the identity of a user, while authorization is the process of determining what resources or actions a user is allowed to access. These processes are essential to ensuring that only authorized individuals can access sensitive company data.
There are several protocols available to implement authentication and authorization like OAuth2 and OIDC.
OAuth2 and OpenID Connect
OAuth2 is an authorization framework that enables third-party applications to obtain access to some resources on behalf of a user, without the user having to disclose their credentials. For example with OAuth2, you can grant permission to the third-party app to access your Google Drive files, without giving the app your Google username and password.

OpenID Connect builds on top of OAuth2 to provide authentication capabilities, allowing users to authenticate themselves with a third-party identity provider.
Here’s an example of how OIDC works in practice:
Let’s say you want to log in to a website that supports OIDC. When you click the “login” button, the website redirects you to an OIDC provider (e.g., Google, Microsoft, or Facebook).
The OIDC provider prompts you to enter your username and password, and then verifies your identity. Once your identity is verified, the OIDC provider sends an access token back to the website that contains information about you (name, email, and profile picture).
The website can then use this access token to authenticate you and authorize access to its resources. The website can also use the access token to personalize your experience (showing your name and profile picture).
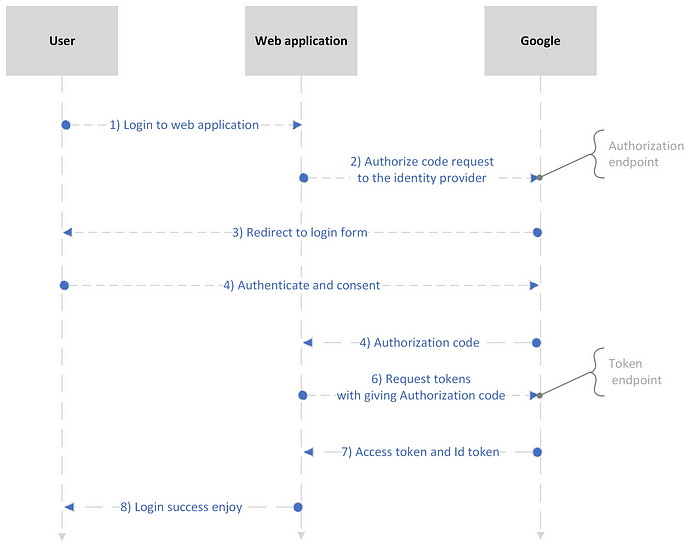
As you can see, The authorization code, access token, endpoints and ID token are all important components of OAuth2 and OpenID Connect (OIDC) protocols.
Authorization Code vs Access Token vs ID Token
- The Authorization Endpoint is a URL endpoint where the user is redirected to start the authorization process. The Authorization Endpoint is owned by the Authorization Server and is responsible for presenting the authorization request to the user, verifying the user’s identity, and obtaining the user’s consent to grant the requested permissions to the client.
- The authorization code is a temporary code that is used in the OAuth2 protocol to authenticate and authorize third-party applications to access user resources. Once the user grants permission, the authorization code is exchanged for an access token.
- The Token Endpoint is a URL endpoint that is used by client applications to exchange an Authorization Code, Refresh Token, or other credentials for an Access Token.
- The access token is a credential that is issued by the authorization server to the third-party application after the user grants permission. The access token is used by the third-party application to access specific resources on behalf of the user. The access token can be either short-lived or long-lived and can have different scopes, which define the specific permissions granted to the third-party application.
- The ID token is a JSON Web Token (JWT) that is used in the OIDC protocol to provide additional information about the user. The ID token contains information such as the user’s name, email address, and other user profile data. The Id token is used to create a claims identity and stored as an authentication ticket an encrypted cookie. It is typically used by the client application to verify the identity of the user and to retrieve additional information about the user.
JWT in Depth
A JWT consists of three parts: a header, a payload, and a signature. The header contains information about the type of token and the cryptographic algorithm used to sign the token. The payload contains the claims, or statements, about the subject (usually the user) and additional data. The signature is used to verify the authenticity of the token and ensure that it has not been tampered with.
Below is an example of JWT from jwt.io web site:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5cThis JWT consists of three parts separated by dots:
- The header:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9 - The payload:
eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ - The signature:
SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
The header specifies that the token is a JSON Web Token (JWT) and that it is signed using the HMAC SHA256 algorithm. The payload contains claims about the user, including their ID ("sub": "1234567890") and name ("name": "John Doe"). The signature is used to verify the authenticity of the token.
In practice, a JWT would be generated and sent to the client upon successful authentication, and then included in subsequent requests to the server. The server would then verify the signature to ensure that the token has not been tampered with and use the information in the payload to authorize the user’s requests.
One of the main characteristics of tokens is that they have a limited lifetime, after which they expire and can no longer be used to access protected resources. When the access token expires, the user typically needs to log in again to obtain a new one. However, if a refresh token is provided, the user can use it to obtain a new access token without the need to log in again.
Refresh Token
A refresh token is a special type of token that is used in the OAuth2 protocol to obtain a new access token without the need for the user to re-authenticate. The refresh token is typically longer-lived than the access token, often lasting several days or weeks.
Securing applications with protocols like OAuth2 and OpenID Connect can be a complex and challenging task, as there are many different components involved in the process, including authentication and authorization, access tokens, Id Tokens, and various protocols for exchanging information between different systems. Ensuring that all of these components can be challenging.
That’s why it is recommended to use an Identity Provider.
Identity Provider
An Identity Provider (IdP) is a system that manages digital identities and provides authentication and authorization services to other applications. An IdP can handle the complexities of protocols like OAuth2 and OpenID Connect, providing a secure and reliable mechanism for managing access to resources.
Some of the famous Identity Providers are: Okta, Microsoft Azure AD, Google Cloud Identity, Keycloak, Auth0 and Identity Server.
Conclusion
In conclusion, authentication and authorization are essential components of securing modern applications. With the rise of OAuth2 and OpenID Connect, managing and securing user identities has become a complex task that requires careful coordination between different components. However, with the use of identity providers, this task can be simplified and made more efficient. By implementing best practices in identity and access management, organizations can ensure that their applications and users are protected from security threats.
